Background
Office
NSA 2400, SonicOS 5.9.0.8-1o
Wan IP: 202.101.101.101
Lan IP: 192.168.1.254/23
TK5 Tunnel IP(TI2): 10.1.0.1
NC1 Tunnel IP(TI3): 10.2.0.1
Branch
TZ300, SonicOS 6.5.4.7-83n & 6.5.4.6-79n
All Branch Lan Subnet in 10.100.0.0/16
NC1:
Lan Subnet 10.100.1.0/24, Wan IP: 119.1.1.1., Tunnel IP: 10.1.0.254
TK5:
Lan Subnet 10.100.2.0/24, Wan IP: 61.2.2.2, Tunnel IP: 10.2.0.253
Start to config
Office Sonicwall
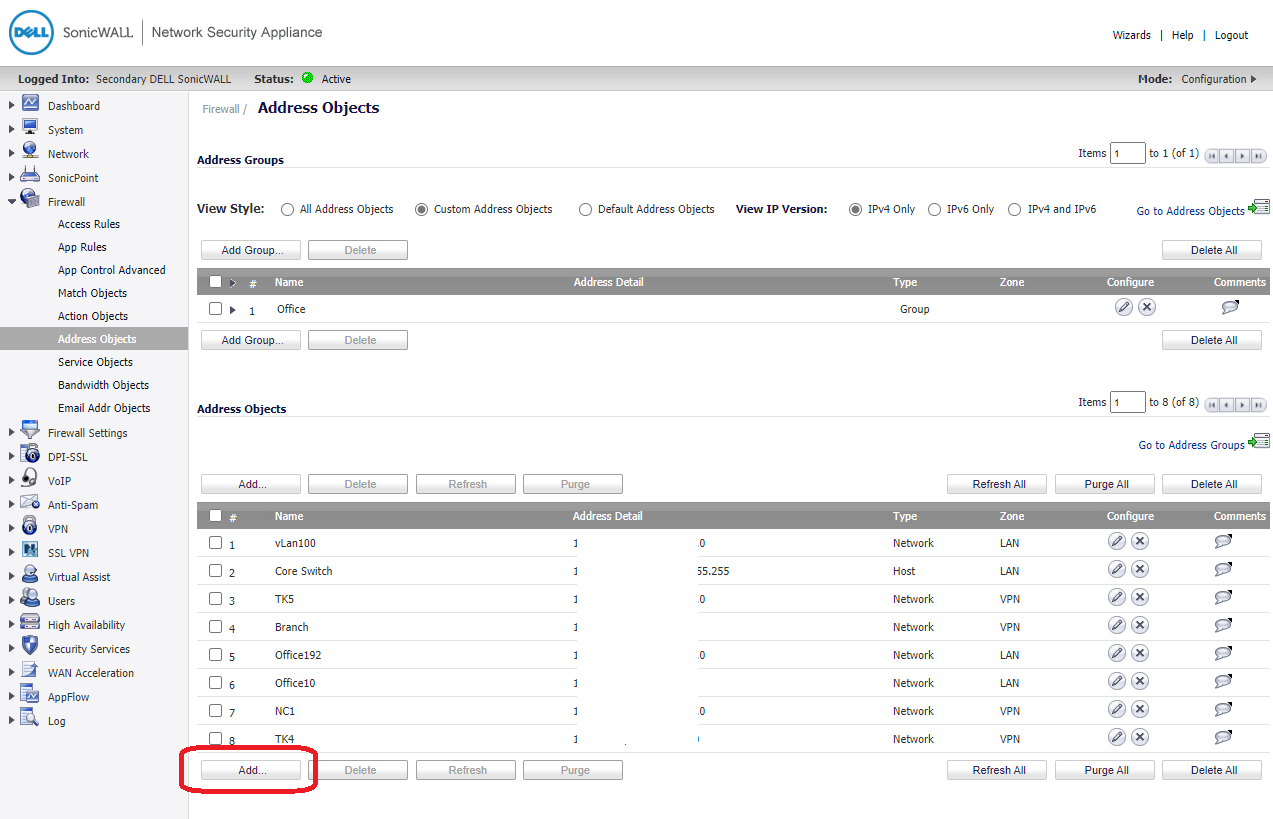
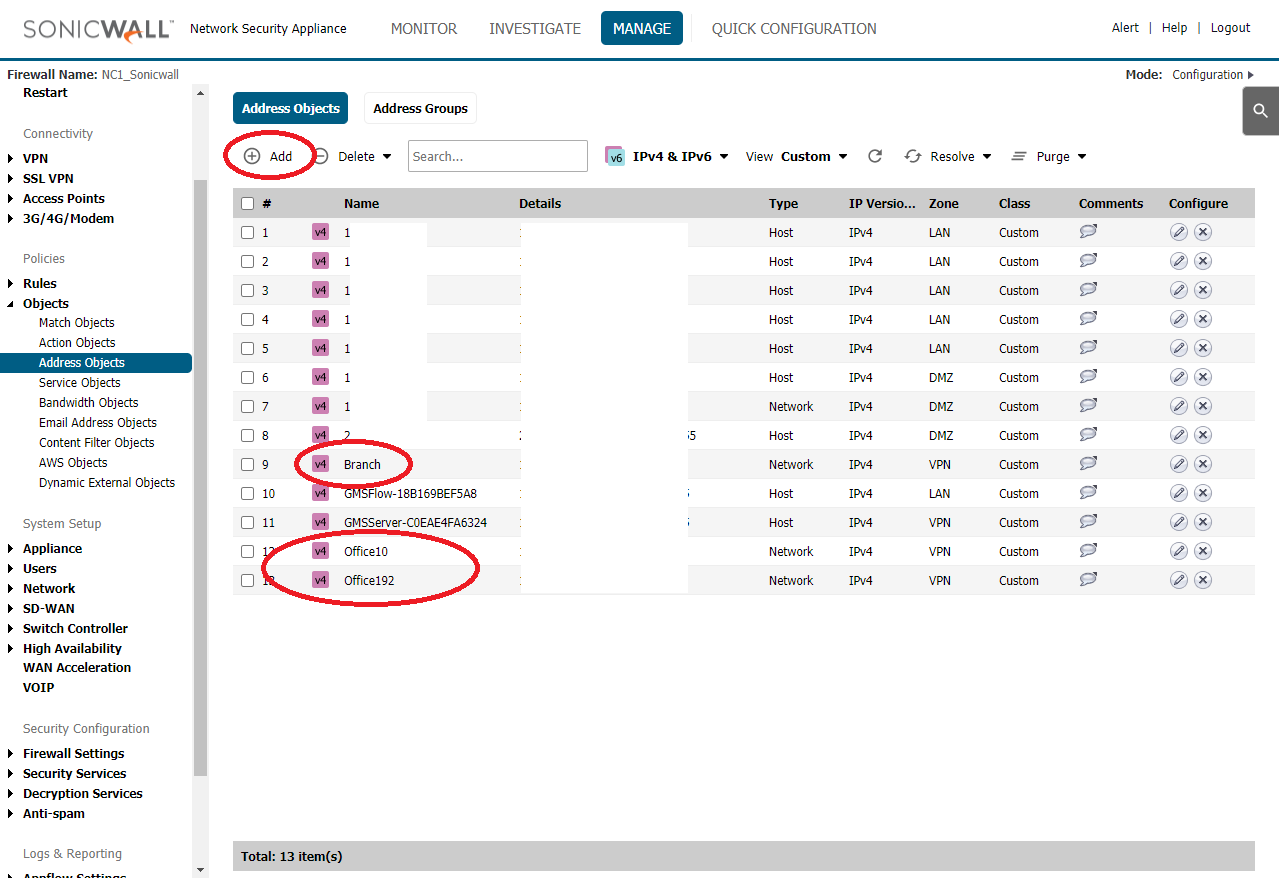
Add all Branch Address Object
Branch 10.100.0.0/255.255.0.0 Network VPN
NC1 10.100.1.0/255.255.255.0 Network VPN
TK5 10.100.2.0/255.255.255.0 Network VPN
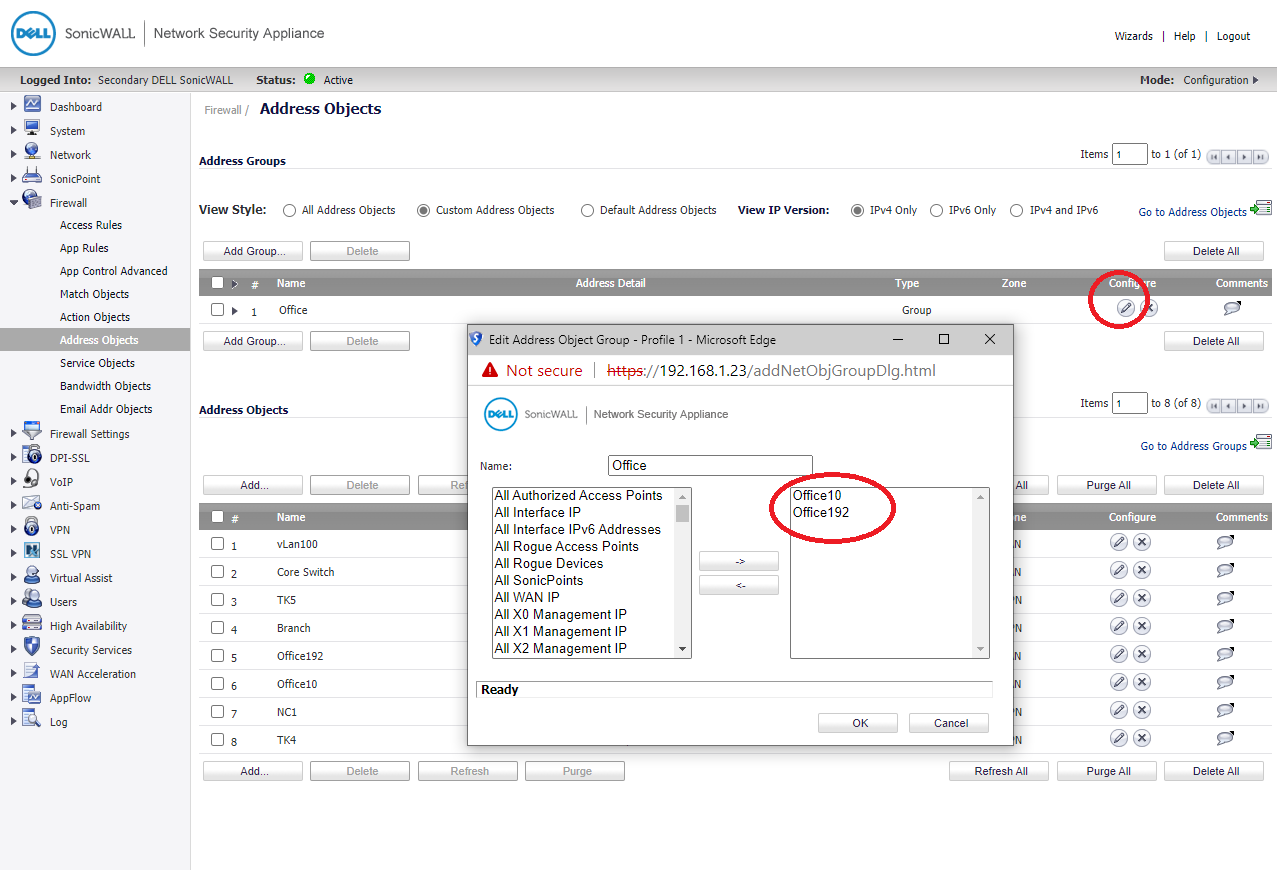
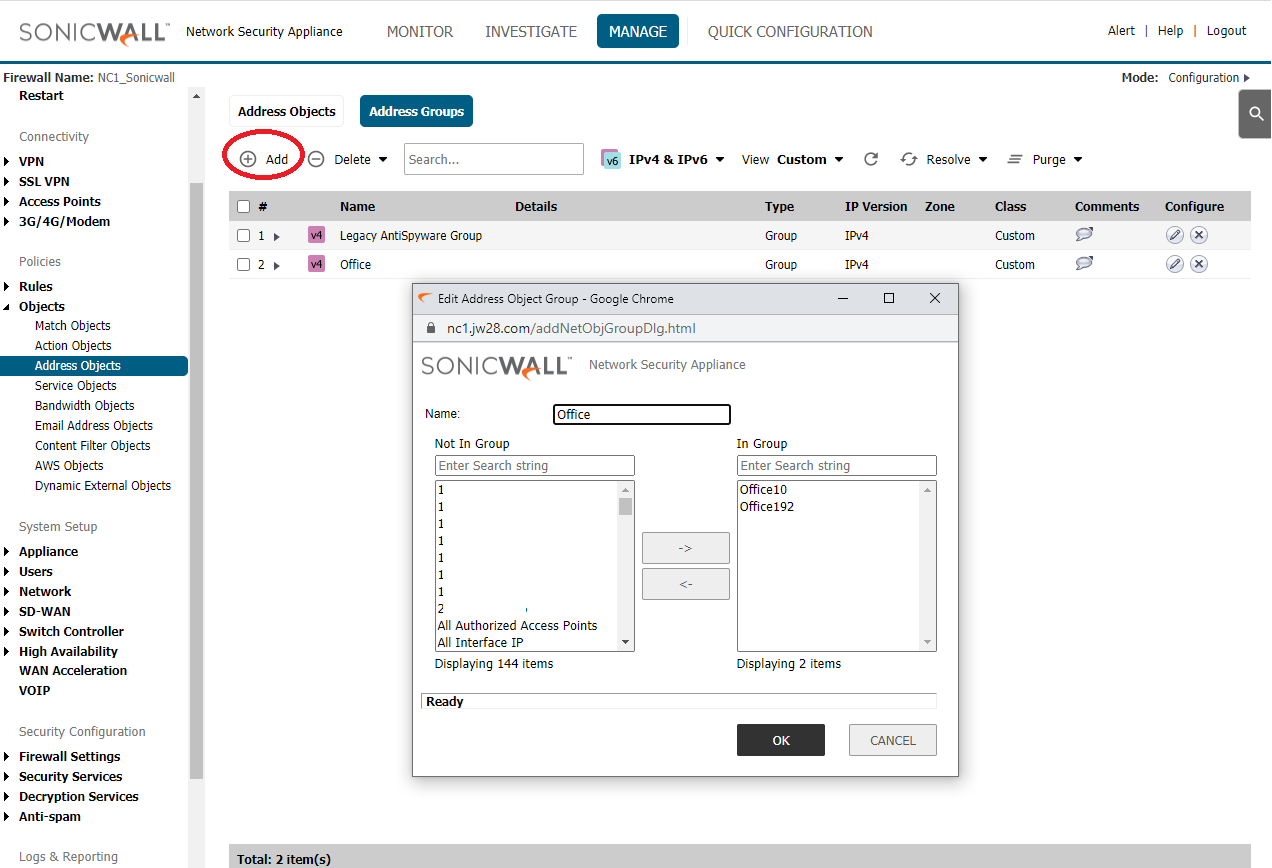
Add Office group including Office vLan
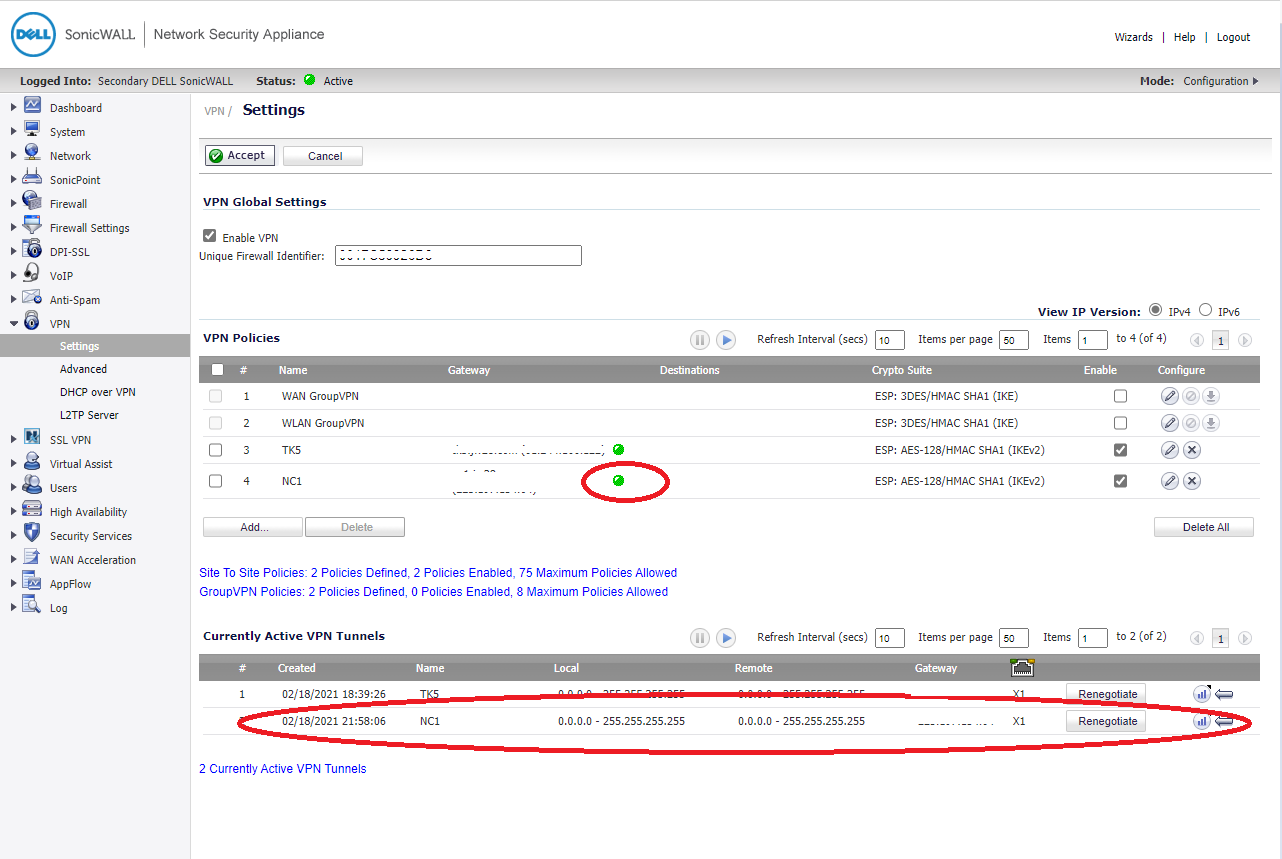
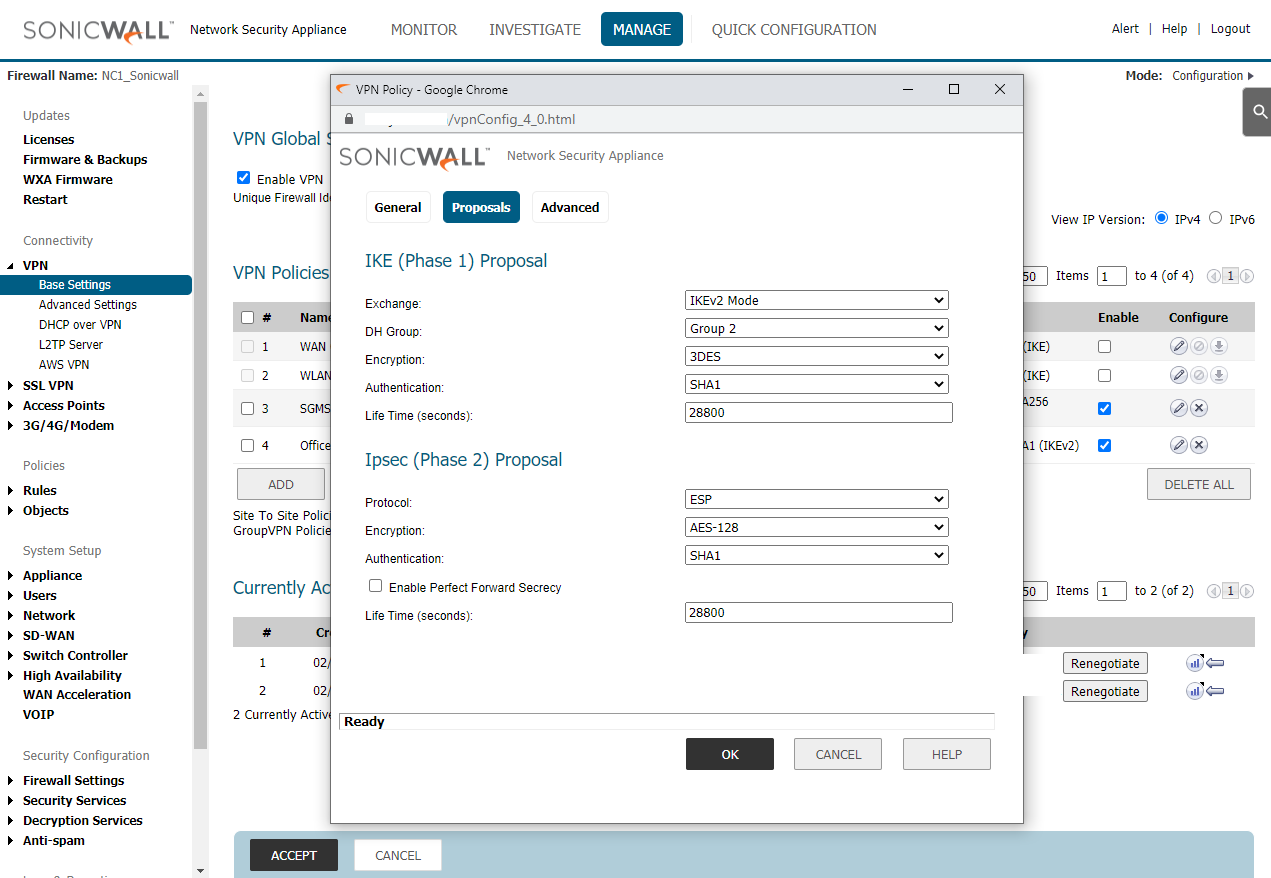
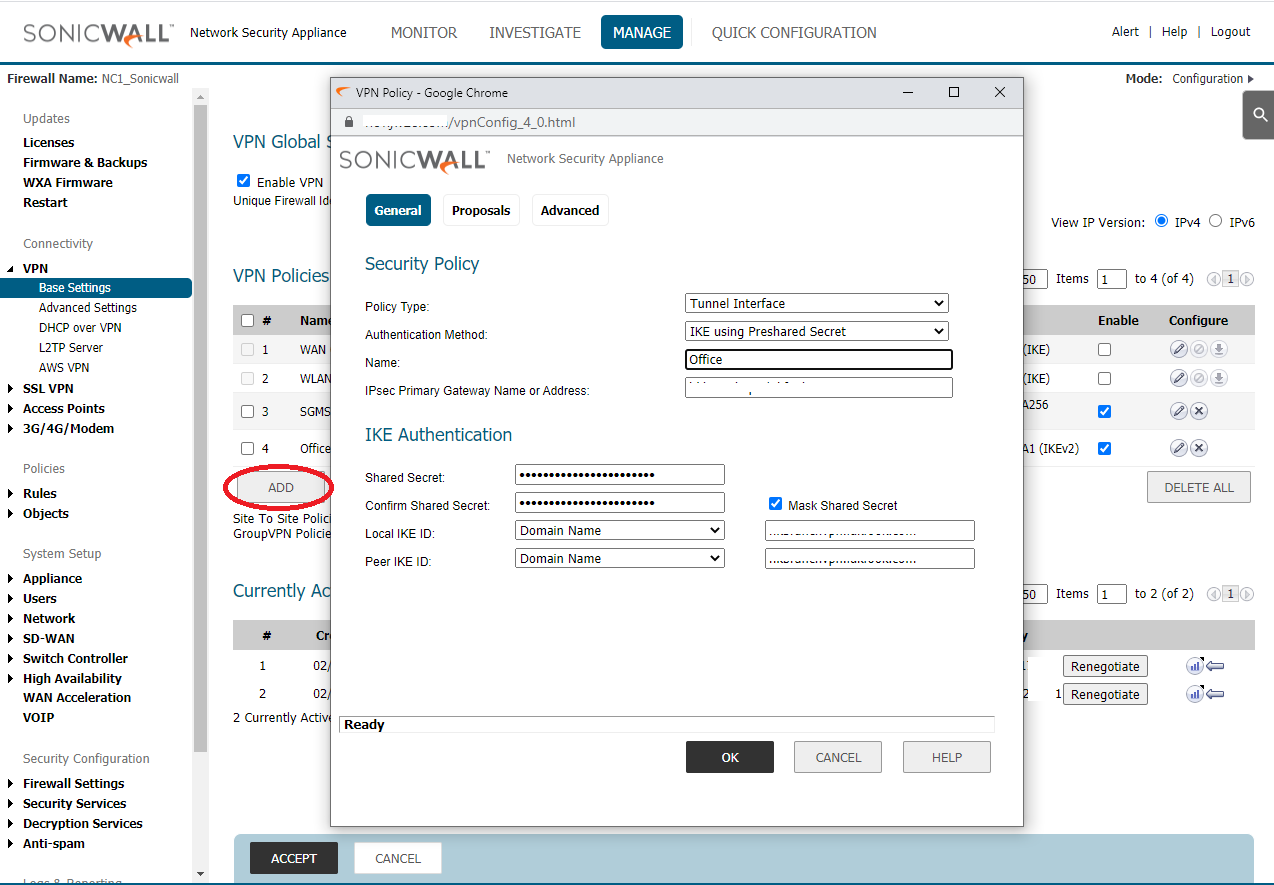
Add VPN Policy
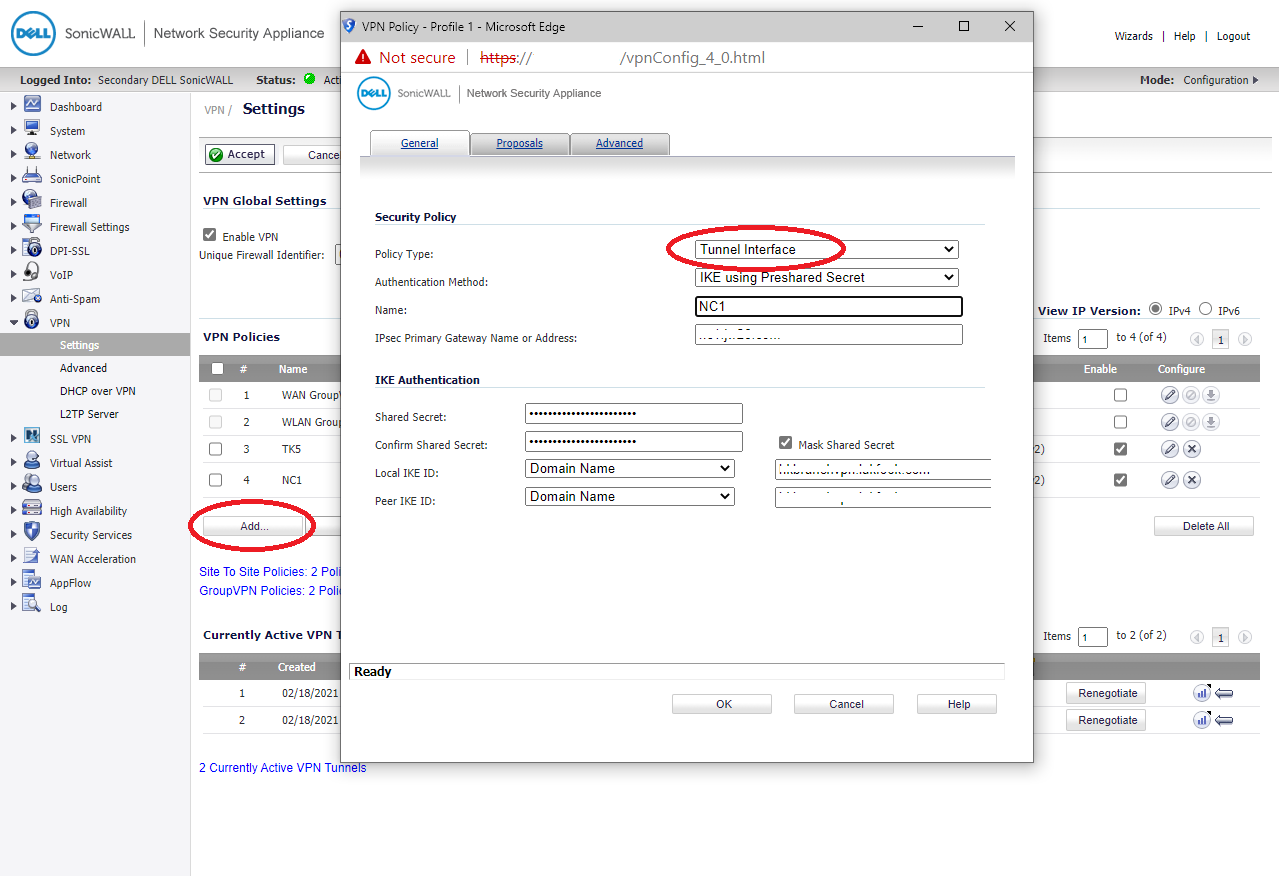
Add a new VPN Policy and change to Tunnel Interface
IPSec Primary Gateway enter NC1 WAN IP
Shared secret same with NC1
Office "Local IKE ID" equal NC1 "Peer IKE ID"
NC1 "Peer IKE ID" equal Office "Local IKE ID"
This lab are same in Local & Peer
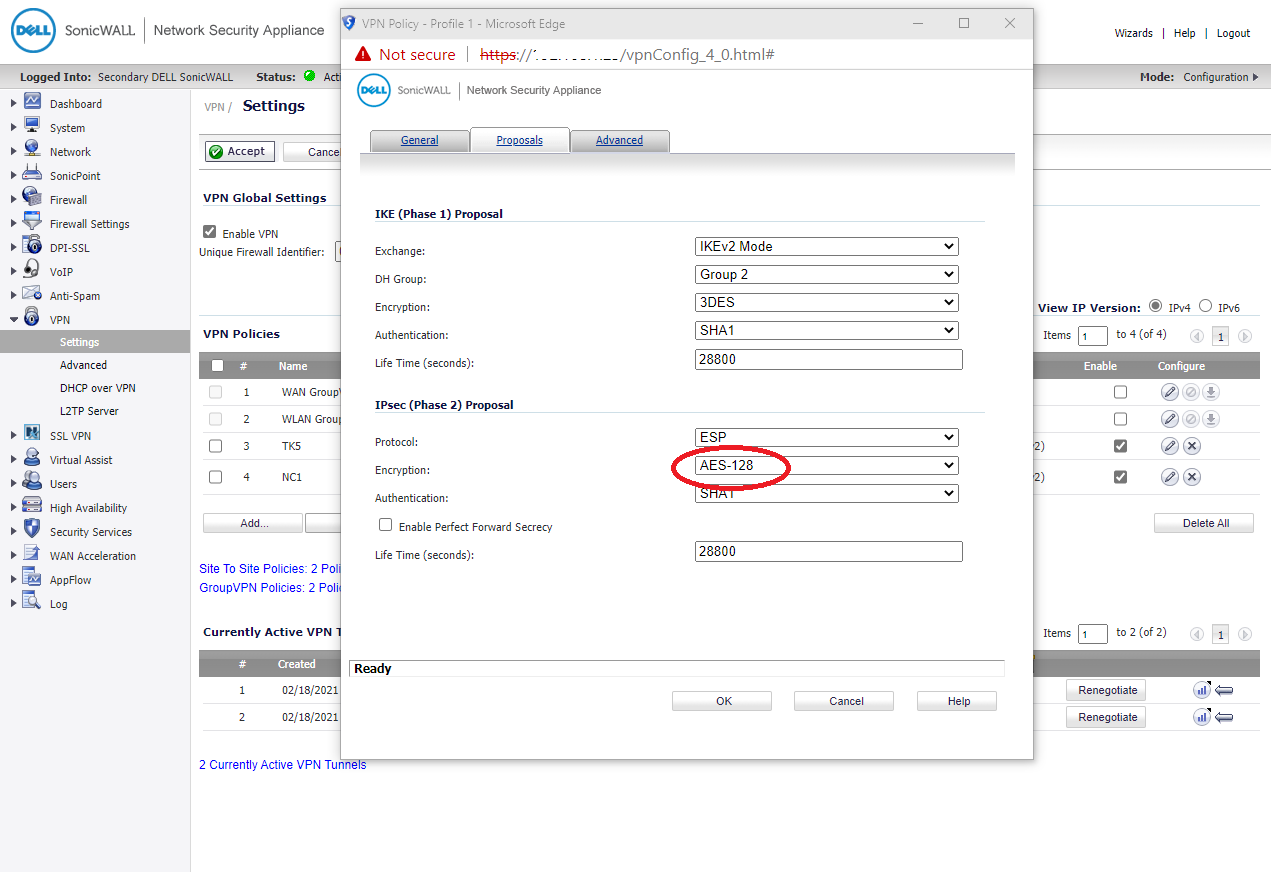
SonicOS 5.9 default Phases 2 Encryption not the same with SonicOS 6.5
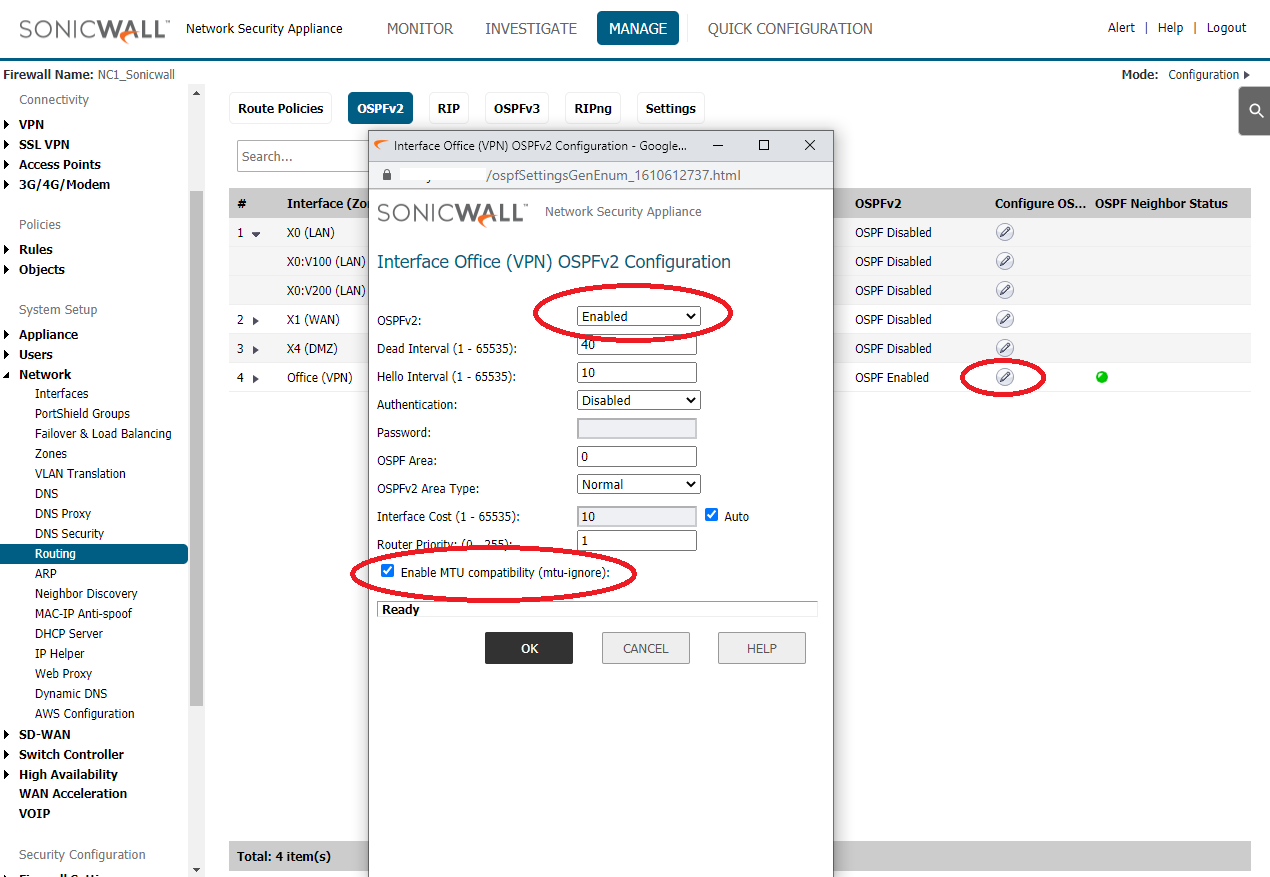
If NC1 configure correctly will show green light
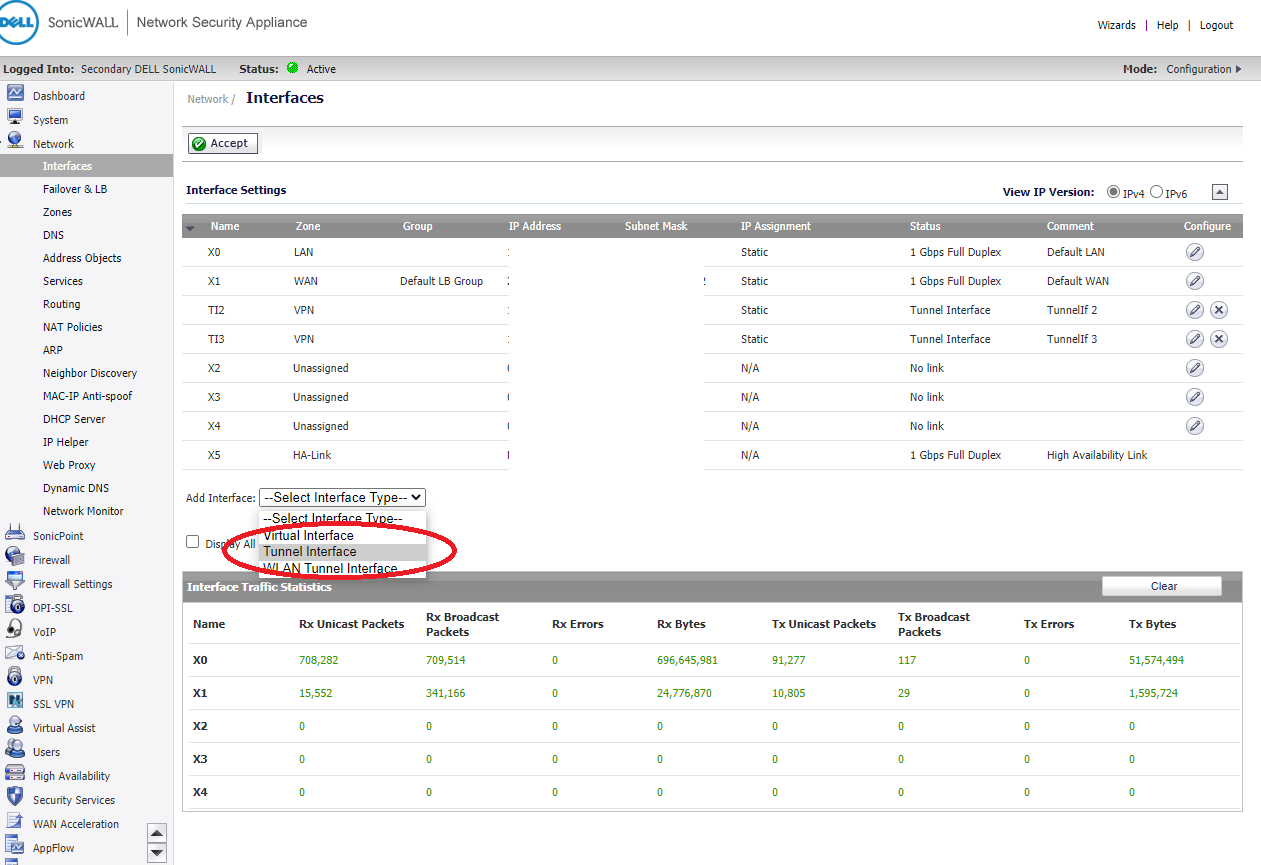
Go to
Network -> Interfaces
Add Interface -> Tunnel Interface
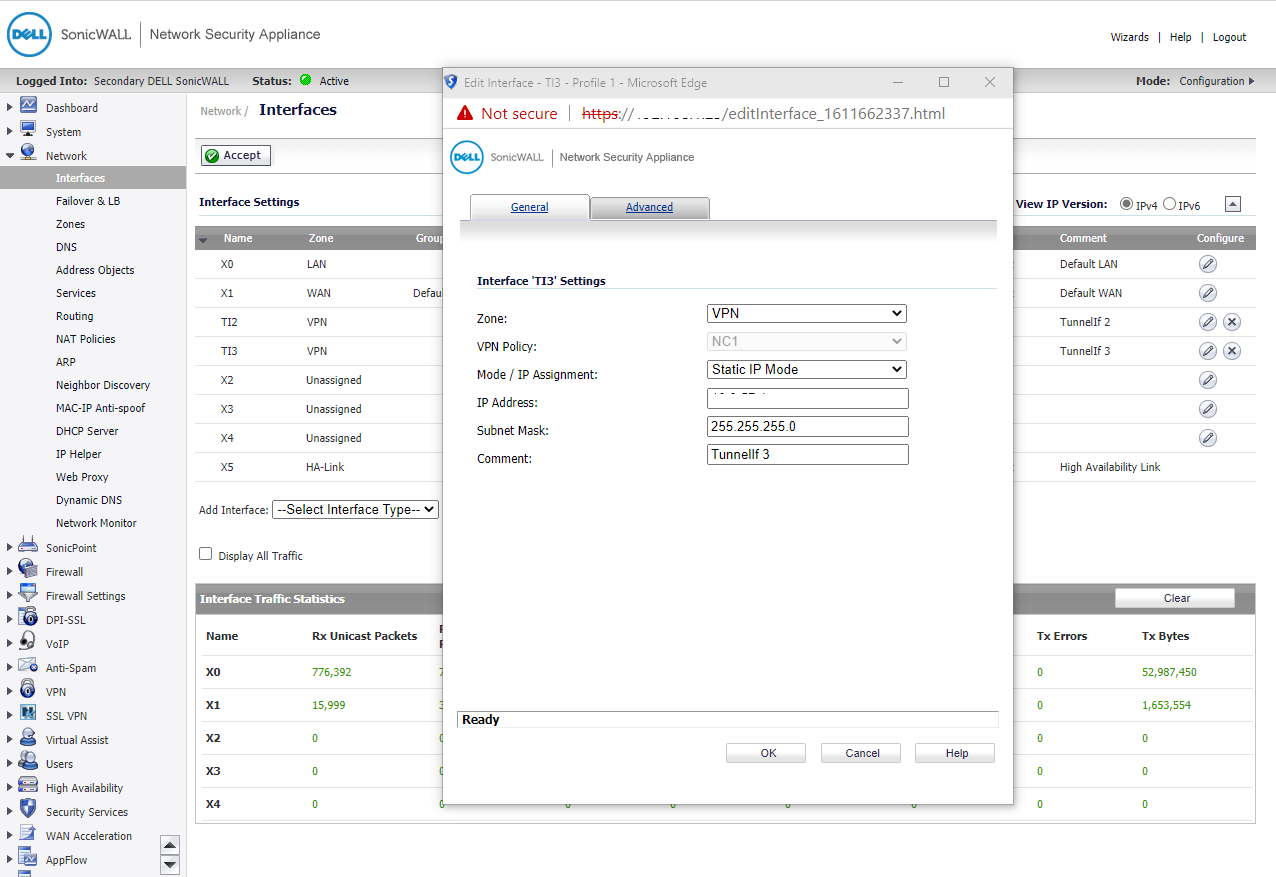
This case enter a new Tunnel IP(TI3) 10.2.0.1
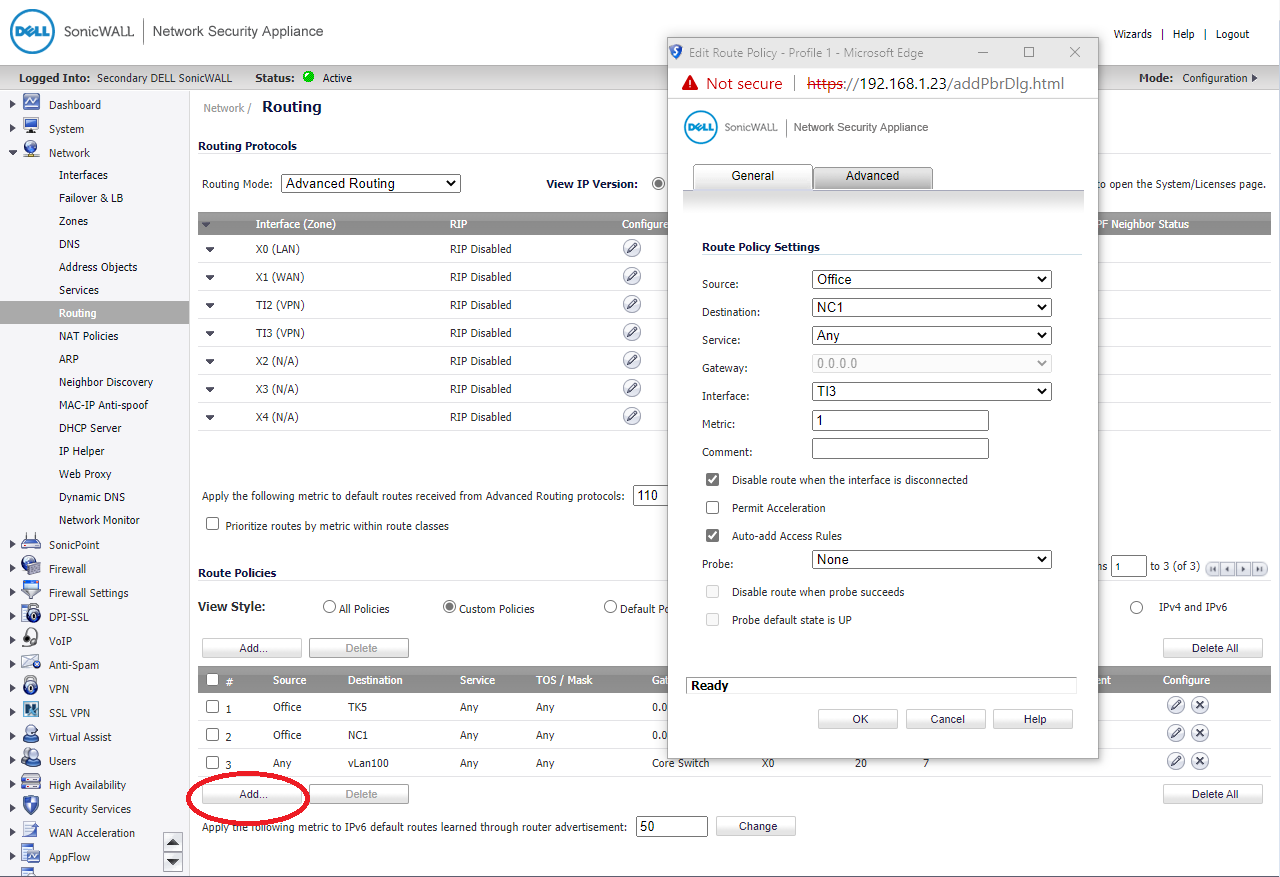
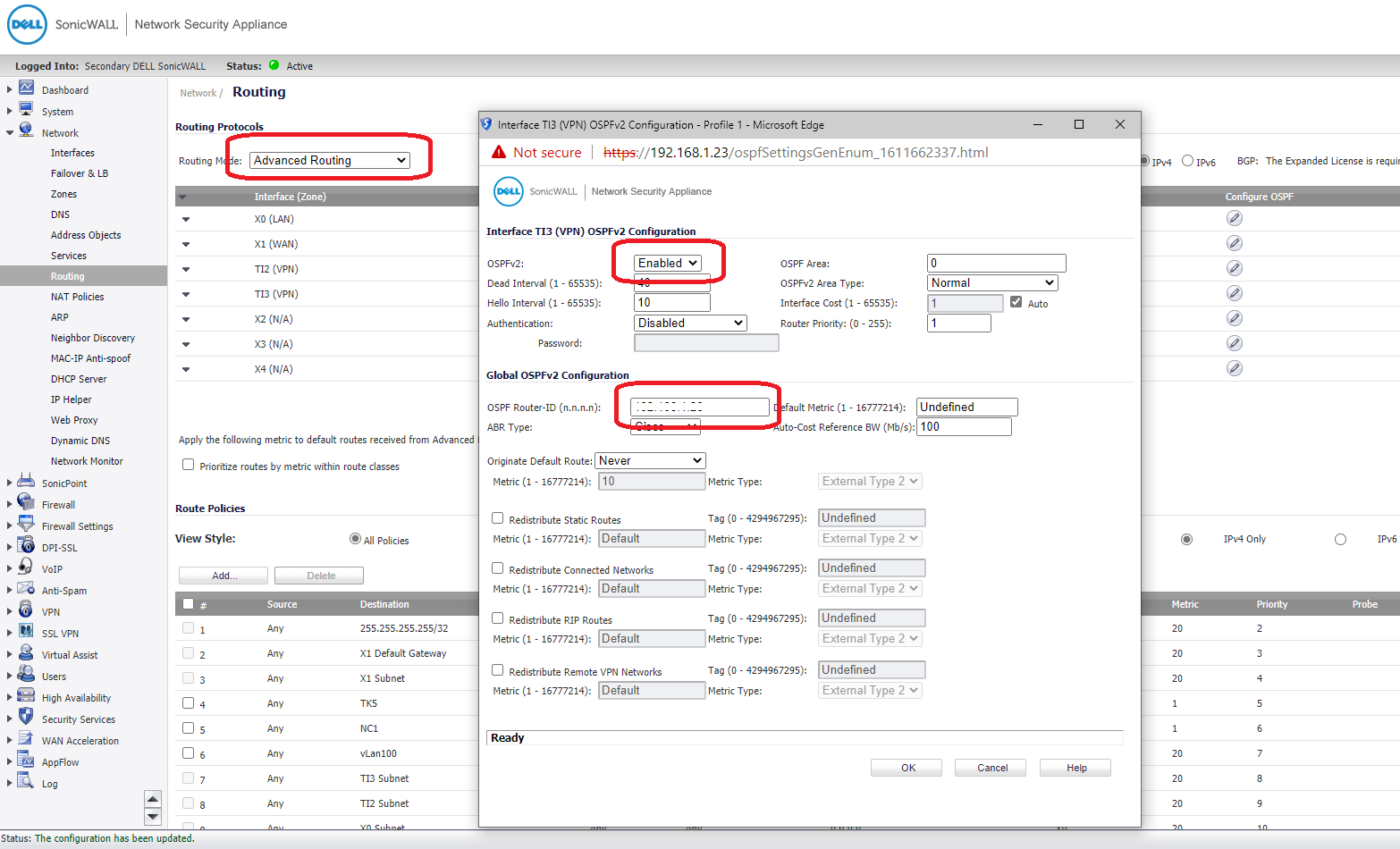
Add routing table
Enable OSFP let branch to learn every Lan subnet
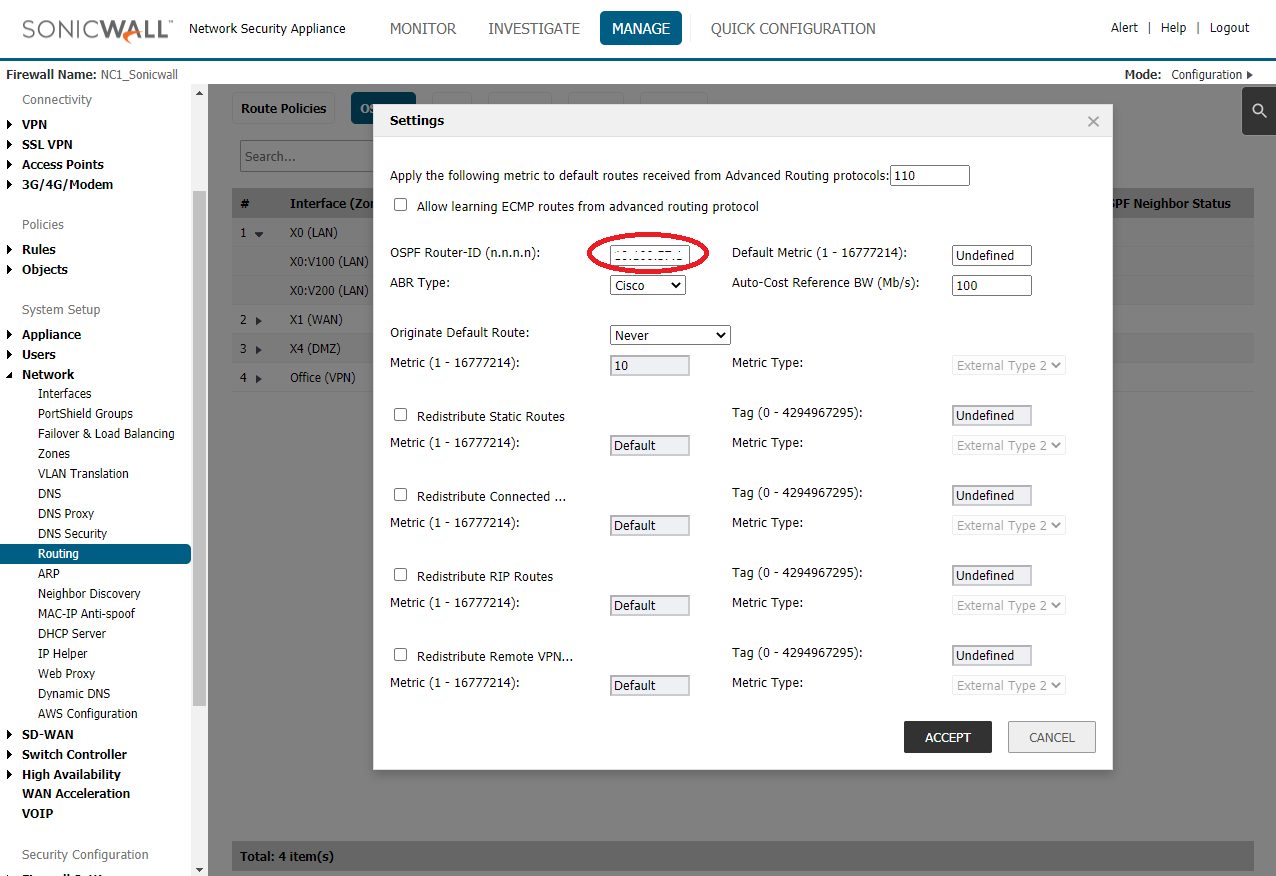
OSPF Router-ID different then all Branch IP, this case we enter Lan IP: 192.168.1.254
Branch Sonicwall
Add Office vLan & a Branch Address Object
Branch 10.100.0.0/255.255.0.0 Network VPN
Office10 10.10.10.0/255.255.255.0 Network VPN
Office192 192.168.0.0/255.255.254.0 Network VPN
do the same thing with office
Tunnel IP 10.2.0.1
Router ID can be Lan IP 10.100.1.254