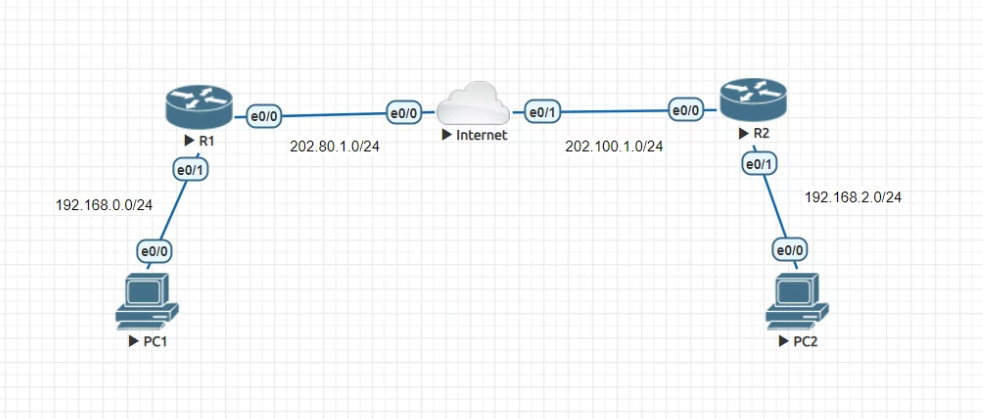
基本Topology設定
PC1
no ip routing ip default-gateway 192.168.0.254 int e0/0 no shut ip add 192.168.0.11 255.255.255.0
PC2
no ip routing ip default-gateway 192.168.2.254 int e0/0 no shut ip add 192.168.2.11 255.255.255.0
Internet
int e0/0 no shut ip add 202.80.1.2 255.255.255.0 int e0/1 no shut ip add 202.100.1.2 255.255.255.0 router eigrp 1 no auto network 202.80.1.0 0.0.0.255 network 202.100.1.0 0.0.0.255
R1
int e0/0 no shut ip add 202.80.1.1 255.255.255.0 int e0/1 no shut ip add 192.168.0.254 255.255.255.0 router eigrp 1 no auto network 202.80.1.0 0.0.0.255
R2
int e0/0 no shut ip add 202.100.1.1 255.255.255.0 int e0/1 no shut ip add 192.168.2.254 255.255.255.0 router eigrp 1 no auto network 202.100.1.0 0.0.0.255
設定好以上的IP和Routing後 R1已經可以ping 202.100.1.1, R2可以ping 202.80.1.1, 下面再設定沒有加密的Tunnel
R1
int t0 ip add 10.0.0.1 255.255.255.252 tunnel source 202.80.1.1 tunnel destination 202.100.1.1 ip route 192.168.2.0 255.255.255.0 t0
R2
int t0 ip add 10.0.0.2 255.255.255.252 tunnel source 202.100.1.1 tunnel destination 202.80.1.1 ip route 192.168.0.0 255.255.255.0 t0
設定好之後PC1可以ping到PC2, 之後我們再設定加密的部份
1. 先設定一個Transform-set
2. 再設定ikev2 profile
3. ipsec profile
4. 使Tunnel0使用ipsec profile
R1
crypto ipsec transform-set VPN_test_transform-set esp-aes 256 esp-sha-hmac crypto ikev2 keyring VPN_test_keyring peer 202.100.1.1 address 202.100.1.1 pre-shared-key 0987654321 crypto ikev2 profile VPN_test_profile match address local interface e0/0 match identity remote address 202.100.1.1 255.255.255.255 authentication local pre-share authentication remote pre-share keyring local VPN_test_keyring crypto ipsec profile VPN_test set transform-set VPN_test_transform-set set pfs group2 set ikev2-profile VPN_test_profile interface Tunnel0 ip unnumbered e0/0 ip virtual-reassembly in ip tcp adjust-mss 1350 tunnel source e0/0 tunnel mode ipsec ipv4 tunnel destination 202.100.1.1 tunnel protection ipsec profile VPN_test
R2
crypto ipsec transform-set VPN_test_transform-set esp-aes 256 esp-sha-hmac crypto ikev2 keyring VPN_test_keyring peer 202.80.1.1 address 202.80.1.1 pre-shared-key 0987654321 crypto ikev2 profile VPN_test_profile match address local interface e0/0 match identity remote address 202.80.1.1 255.255.255.255 authentication local pre-share authentication remote pre-share keyring local VPN_test_keyring crypto ipsec profile VPN_test set transform-set VPN_test_transform-set set pfs group2 set ikev2-profile VPN_test_profile interface Tunnel0 ip unnumbered e0/0 ip virtual-reassembly in ip tcp adjust-mss 1350 tunnel source e0/0 tunnel mode ipsec ipv4 tunnel destination 202.80.1.1 tunnel protection ipsec profile VPN_test
發生問題時, 我曾試用下面指令尋找原因
debug tunnel
show crypto ikev2 sa
show crypto ipsec sa
show crypto session detail